Throughout the COVID-19 pandemic, businesses that weren’t outright forced to close experienced significant operations disruptions, as quarantine measures required small businesses to adopt remote work and hybrid arrangements with little up-front preparation. While this shift away from working in the office has led to safer work conditions, improved productivity, and provided other benefits to the employees, it has also led to an unanticipated increase in cybersecurity incidents. Professionals managing the cybersecurity for small businesses especially have been challenged by a workforce no longer under the protection of the managed office space network and a significant uptick in cyberattacks specifically targeting small businesses.
It has become clear that small businesses and service providers are maintaining work-from-home and hybrid arrangements as the economy continues to adapt to COVID-19. UpCity decided to explore how small businesses are handling their cybersecurity efforts in 2022 compared to pre-COVID.
We’ve divided the discussion into three sections:
- Cybersecurity Plans, Resources, and Budgets
- Small Business Cybersecurity Attacks
- Cybersecurity Threat Preparation and Prevention Measures
The importance of cybersecurity readiness cannot be conveyed solely through data and analytics. Therefore, UpCity has folded in insight and guidance from small business owners and cybersecurity experts themselves into this survey discussion in order to provide better insight into how your business can protect itself in 2022.
Cybersecurity Plans, Resources, and Budgets
50% of U.S. small businesses have a cybersecurity plan in place for 2022
Malicious actors have assuredly gotten the attention of small businesses across industries. Moving into the second quarter of 2022, 80% of survey respondents either already have a plan in place or plan to initiate a cybersecurity plan by the end of the year. However, that leaves 20% of our respondents with no protection from attack and another 30% exposed until they initiate a proper plan for training staff and securing their systems. Despite the risks, small businesses often claim a lack of funds or resources, especially throughout and in the wake of COVID-19, to properly invest in cybersecurity measures, especially measures directed at a remote workforce.

50% – Yes, we currently have a cybersecurity plan that we stand by
30% – We don’t currently have a cybersecurity plan, but we intend to create one in 2022
20% – We don’t currently have a cybersecurity plan, and we don’t intend to create one in the foreseeable future
42% of respondents have revised their cybersecurity plan since the COVID-19 pandemic
When employees are working within the office, small business cybersecurity professionals are able to better secure data and the organization’s network because all of the devices in use are owned and managed by the IT team. The integrity of many small businesses’ IT systems was compromised when the pandemic forced small business owners to open their doors to work-from-home or hybrid work arrangements in order to remain operational. Few were prepared with the resources and equipment necessary to support the exodus into the field, so many employees have been allowed to use personal devices and personal networks in order to maintain business continuity.
With this shift to bring-your-own-device (BYOD) and the use of unsecured or partially secured networks, many small business owners are working with their cybersecurity teams to modify their security policies around device and network usage. Beyond the 42% of our respondents who revised their plans, an additional 27% of respondents were forced to implement cybersecurity measures in order to mitigate the additional risks of operating post-COVID.

27% – I didn’t have a cybersecurity plan before the COVID-19 pandemic
42% – I had a cybersecurity plan in place pre-COVID and revised my plan now in 2022
32% – My cybersecurity plan hasn’t changed since the pandemic
Let’s take a look at this from the operations and management point of view to find out how professionals were handling cybersecurity before the pandemic, and how they’ve shifted tactics in the months since in their efforts to maintain operations.
“Our company has had a cybersecurity plan since the creation of our company. It is not wise to develop a presence online without proper cybersecurity measures. The pandemic made cybersecurity concerns slightly more tedious because we had to work with remote aspects of security measures. Covid forced us to be on top of an individual’s internet capabilities, and whether they could work from a safe server from home. Luckily, there is an abundance of cybersecurity software systems that allow us to go about protecting our team and our employees in the best way possible!”
—Nick Mueller, Director of Operations, HawaiianIslands.com
“Yes, my company had a cybersecurity plan in place before the pandemic. It is important for all businesses to have a cybersecurity plan set in place, regardless of their size, but seeing as cybersecurity is a big part of what my company educates the public on, it would be hypocritical if we didn’t have our own plan! However, we have gained a much larger audience and have scaled up our team as well, so our plan had to be scaled up accordingly. So while we didn’t re-start from scratch, we definitely added on some new things and perfected it more. It’s important to always aim for improving and strengthening your cybersecurity efforts, especially as risks increase.”
—Kristen Bolig, Founder, SecurityNerd
“Anytime you’re dealing with sensitive customer information, you should have a cybersecurity plan in place. Add in another threat level of your employees working remotely and, consequently, on unsecured networks and you have a need for an even stronger cybersecurity plan. While we didn’t change much to our overall cybersecurity plan, we did make sure that every team member was using best practices for online security (i.e. strong passwords, multi-factor authentication, and secure networks) once we went to a fully remote model for the pandemic. We were already a hybrid workplace before the pandemic, so there wasn’t much of an adjustment. More of a tightening up of best practices to ensure online security.”
—Brian Donovan, CEO, Timeshatter
37% of respondents revised their plan by investing in new cybersecurity technologies/products
The scope necessary to secure employee online activities remotely means that security teams must now monitor and secure the online activity of employees interacting virtually with company assets. This shift in security priorities to a remote workforce has led to small business cybersecurity teams having to adopt and implement more complex protocols for maintaining and managing security across a much larger attack surface.
The skills to use the necessary technologies or handle new types of threats are not always standard for in-house teams, which has led small businesses to expand their teams or outsource to service providers with the skills and capabilities of their cybersecurity team. For those with a skilled and capable team in place, our respondents showed a trend toward increasing their investment in new technologies and tools that help them expand their capabilities.
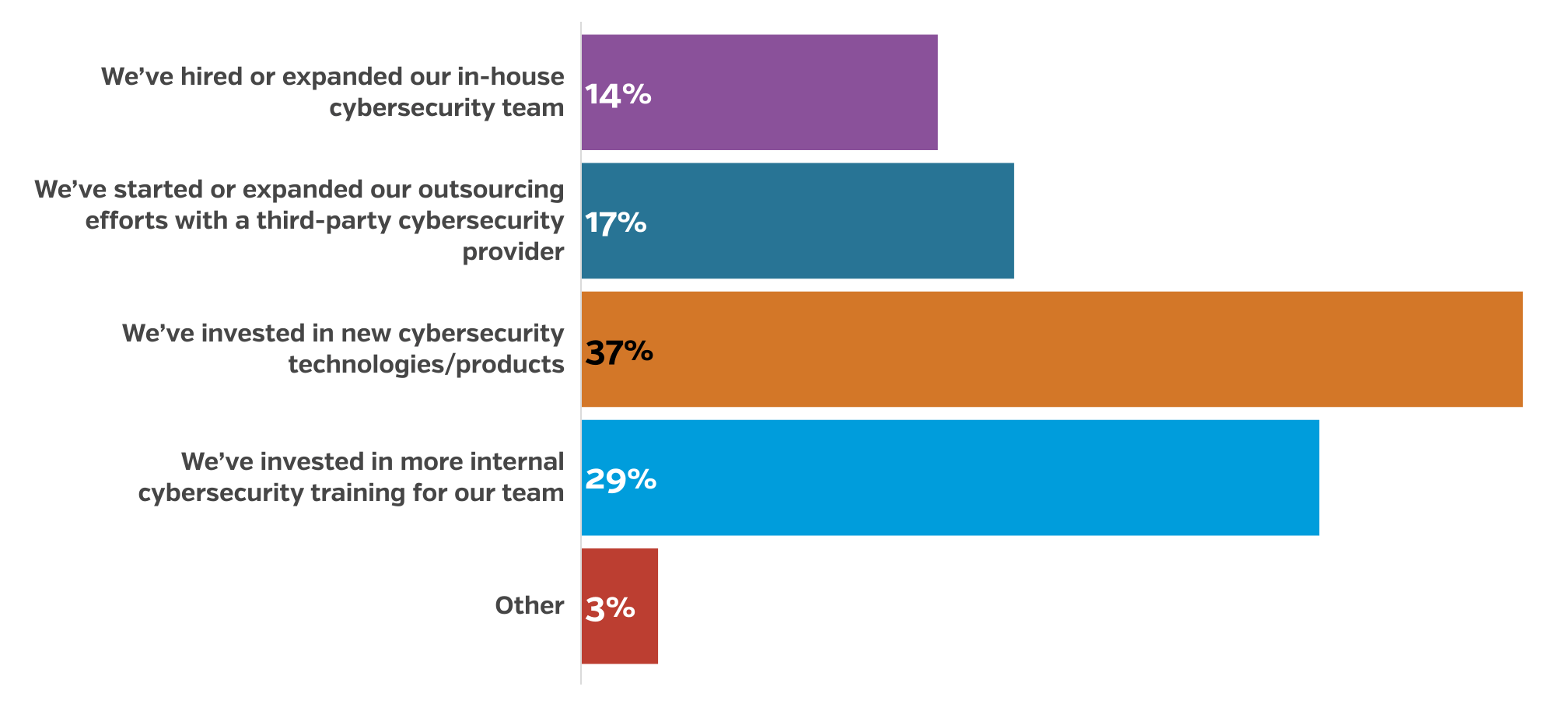
14% – We’ve hired or expanded our in-house cybersecurity team
17% – We’ve started or expanded our outsourcing efforts with a third-party cybersecurity provider
37% – We’ve invested in new cybersecurity technologies/products
29% – We’ve invested in more internal cybersecurity training for our team
3% – Other
“This statistic doesn’t surprise me. I wish it was a much higher metric (ideally 100%) as that would dramatically reduce the impact and frequency of data breaches. Fundamentally, there is a large segment of business leadership that doesn’t understand or want to invest in cyber protection. Unfortunately, some folks need to get hit before they will commit the dollars. It’s also similar to getting on a health regimen. Some people go for the fad diet and then regain the weight and don’t fix the underlying mindset. Others make substantive changes by modifying their diet, exercising more, and changing their lifestyle. In my opinion, the 37% are those making the fundamental changes. Change is hard and scary; it’s part of the human condition it seems.”
—Rob Schenk, Co-Founder, Intivix
“37% of SMBs is not surprising at all, in fact, I’m a little taken back that the number isn’t higher. Organizations had to quickly switch to a remote workforce, forcing several to catch up on IT debt they incurred over time, they also had to implement secure solutions for remote access and application delivery, all while dealing with the increased cybersecurity attack.
We’re seeing large movements to cloud technologies because of the flexibility and scalability that it offers remote workforces which require different tooling for cybersecurity. Defending the four walls you work in is one thing but defending a device somewhere outside your four walls is entirely different. Cybersecurity solutions switched from the perimeter to the individual user and from the network to the application.”
—Ryan Gould, Director of Solution Engineering, Resultant
“It’s a critical time to ensure that you not only put in place cybersecurity policies, but that you also keep an eye on them to see if they’re being followed. Developing solid regulations and keeping track of compliance can help a company strive toward a more secure environment. It’s crucial to keep track of conformance throughout time. It assists you in avoiding configuration drift away from secure configuration and rapidly identifying any new problems. Tools released by the Center for Internet Security (CIS) can aid in the monitoring of compliance and the identification of flaws. The CIS-CAT Pro Dashboard is a graphical interface for examining the results of CIS Benchmark compliance assessments over time. CIS CSAT Pro, on the other hand, enables an organization to track the execution of the CIS Controls over time.”
—Lanny Tuchmayer, Director of Operations, Bergel Law
“A good cybersecurity plan starts with designing and implementing a thorough training and education program across your organization. This must be done to generate knowledge and skills while establishing a culture where cybersecurity is clearly a company priority. Employees may make security-related decisions and use best practices to safeguard themselves, the company, and its data. It is critical that all employees, especially management and executives, understand cybersecurity basics, so you must include ongoing training for existing staff in your training program. Onboarding sessions should also incorporate education. This will guarantee that all new staff is well-versed in cybersecurity standards.”
—Benjamin Stenson, CEO, Norsemen Home Remodeling
“In building out your cybersecurity strategy, it’s necessary to address several key factors. First, define your objectives and goals. What are you trying to protect, and what are your priorities? From there, you should identify your assets and vulnerabilities. What information and systems are most critical to your organization, and where are the possible weak spots? After establishing your goals and the assets in play, your team can implement security controls. Choose the technical and procedural measures that will help you mitigate risks and protect your assets. You can then communicate and train employees on these protocols. Make sure everyone in your organization knows their roles and responsibilities in keeping data safe. Follow up and provide tools to help your team maintain standards by creating checklists and processes that make it as easy and safe as possible. Test and monitor your system regularly. Check that your security controls are working as intended, and be prepared with a plan to respond to incidents swiftly.”
—Stephen Heffernan, Digital Specialist, The Connected Narrative
25% of small businesses spent less than $500 on their monthly cybersecurity plan Pre-COVID. 26% of users are now investing more heavily in cybersecurity with a monthly budget of $500-$1,499
Adopting new strategies and technologies with the assistance of increased staffing or outsourced personnel necessitated many of our respondents to expand their cybersecurity budgets. While some measures taken might take advantage of free-to-use software or a realignment of internal policies and procedures, expanding staff or outsourcing would necessitate either the shifting of existing expenditures or increased expenses in order to expand training programs, onboard new personnel, and integrate new technologies into the existing IT tech stack.
We can see this trend toward small businesses increasing their cybersecurity budgets in the respondent data showing an increase in the number of organizations spending between $500 and $1,999 to protect their assets. The reasons for decreases at other budgetary levels are uncertain but could be tied to expenditure reductions in larger organizations as a result of reduced revenue streams and the significant number of organizations that haven’t prioritized cybersecurity prior to or in the wake of COVID-19.

| Pre-COVID | 2022 | |
|---|---|---|
| Less than $500 monthly | 25% | 22% |
| $500-$1,499 monthly | 24% | 26% |
| $1,500-$1,999 monthly | 19% | 24% |
| $2,000-$4,999 monthly | 18% | 15% |
| $5,000+ monthly | 9% | 10% |
| Unsure | 6% | 4% |
“We have noticed an incremental increase in small businesses’ willingness to invest in cybersecurity, but most organizations are still not aligning their budgets with their risks. Far too often, small businesses are convinced that cybersecurity is the IT department’s problem, or that a single security product can make their business secure. The reality is that cybersecurity risks are only mitigated when everyone in top-level leadership buys into the necessity of building security into their organization’s culture.”
—David Bryden, CEO, TechMD
“The question of how to budget for cybersecurity is traditionally a hard question to answer. I would ask, what is the digital footprint of the company? Does the SMB have a DoD Supply Chain contract? If no supply chain contract and solely based on digital footprint, I’d suggest the following. First, it’s necessary to understand how the current budget is allocated and then create a full asset inventory on all of your existing contracts, services, licenses, systems, and cloud services. Once you know your existing overhead, it can be broken down in relation to your allocated personnel. Do you have personnel actively doing cyber defense or are you paying for managed security? Once you determine this, you can allocate continuous training into the work environment.
The second issue you have to address is that continuous monitoring and evaluation should be on your mind at all times. The standard checklist drills do not work nearly effectively as passive security practices with social engineering/phishing campaigns to measure your company’s resiliency and hygiene at the personnel level.
Finally, I suggest that all organizations join an Information Sharing and Analysis Organization (ISAO) or Information and Sharing and Analysis Center (ISAC), as doing so a lot of times provides insurance breaks, free training, and other tailored services to your type of business. All of these factors in establishing your monthly budget largely depend on your industry and the size of your business. For example, a smaller company could benefit from an “As a Service” cybersecurity vendor. The type of company could affect the budget when it comes to certain GDPR and HIPPA laws and compliances and should be treated as a monthly concern”
—Paul Cummings, President, Whole Cyber Human Initiative
When we brought the question of budgeting to our community of experts, it became increasingly clear that budgetary adjustments were critical for addressing remote work challenges and the risks that accompany such arrangements. Solutions added to the budgets by many small business owners range from additional secure technology, staff training, and third-party auditing.
“It’s becoming increasingly necessary to budget for data storage. Even the tiniest organization, I believe, currently acquires and maintains sensitive data processes that require the support of appropriate data security methods and technologies, and it is this data that hackers seek. When allocating funds for safe data storage, you must pick between cloud-based storage and on-premise software that includes functions such as version control, document management, archiving, and editing. Taking into account the unique requirements and characteristics of your business, selecting the appropriate solution is critical to the success of your data management procedures.”
—Josh Pelletier, Chief Marketing Officer, BarBend
“When budgeting, appropriate money should be set aside for security awareness and employee training. I feel that it is a truth that the majority of data breaches occur as a result of human error. Regardless of how advanced your tools are or how large your cybersecurity budget is, if your staff are not informed and do not adhere to best practices, you will not receive your money’s value. It is critical to raise staff awareness of security best practices. Security awareness educates individuals about numerous security rules and best practices, such as how to spot phishing emails, how to protect data integrity and confidentiality, and more. Additionally, security awareness training enables you to foster a cybersecurity-friendly culture. As a result, effective security policies become the lifeblood of your operations.”
—Mark Valderrama, Owner & CEO, Aquarium Store Depot
“Budget for vulnerability testing by an expert third party, as well as expert advice on potential dangers for your managers and personnel. Ideally, this budget column should receive adequate funding, allowing you to engage the assistance of more than one expert or team of experts. While you may object to paying for more than one consultant or expert, consider the importance of having a second perspective. The more sensitive the data, the more professionals should assist you in anticipating and mitigating dangers, as well as putting in place the necessary administrative, technical, and physical precautions.”
—Dr. Frederik Lipfert, Founder & CEO, VPNCheck.org
With the rise in cyberattacks on small businesses throughout the COVID-19 pandemic, small business owners have been forced to reconsider their stance relative to cybersecurity. As the workplace has extended beyond office walls into the homes of employees and public spaces, securing employee online activity has become a priority that has required small business owners to increase funding for their cybersecurity teams to onboard new staff, outsource tasks to third-party service providers, and train staff in the use of new technologies.
Next, we’re going to dive into the impact cyberattacks have had on small businesses and ways to mitigate or prevent them.
Small Business Cybersecurity Attacks
43% of small businesses overall noted that they’ve never experienced a cybersecurity attack
While many of our respondents haven’t experienced a cybersecurity attack, it’s more telling that an equal percentage of our respondents were victims of a cyberattack before the pandemic as were victims after COVID-19 forced employees into the field and away from the office. This goes to the heart of the challenges being faced by cybersecurity teams in the field that revolve around the resources small businesses are willing to direct toward cybersecurity and the unwillingness of the leadership in many organizations to fold cybersecurity into risk mitigation and only treat it as a technology shortcoming.
Overall Breakdown

30% – We’ve been the victim of a cybersecurity attack pre-COVID
28% – We’ve been a victim of a cybersecurity attack since the pandemic started
43% – My business has never been the victim of a cybersecurity attack
33% of businesses that have been operating for 3-5 years have been victims of a cybersecurity attack Pre-COVID
Private user data can largely be considered one of the most valuable commodities in the modern economy, so it’s no wonder that cyberattacks historically are largely focused on the illicit acquisition of valuable user data. Knowing the value of user data, it follows that malicious actors have focussed their efforts on compromising the network integrity of small businesses that have been in operation for a year to nine years, with a slight drop-off in businesses operating for more than 10 years. In this window, it’s likely that a profitable level of user data has been acquired by the targets, but the target organizations have not been in operation long enough to have developed mature or robust cybersecurity protocols. While an organization in operation for three to nine years might have more significant resources in play, the value of the data in their systems will be higher due to the amount of time the organization has been in operation.
Years in Business
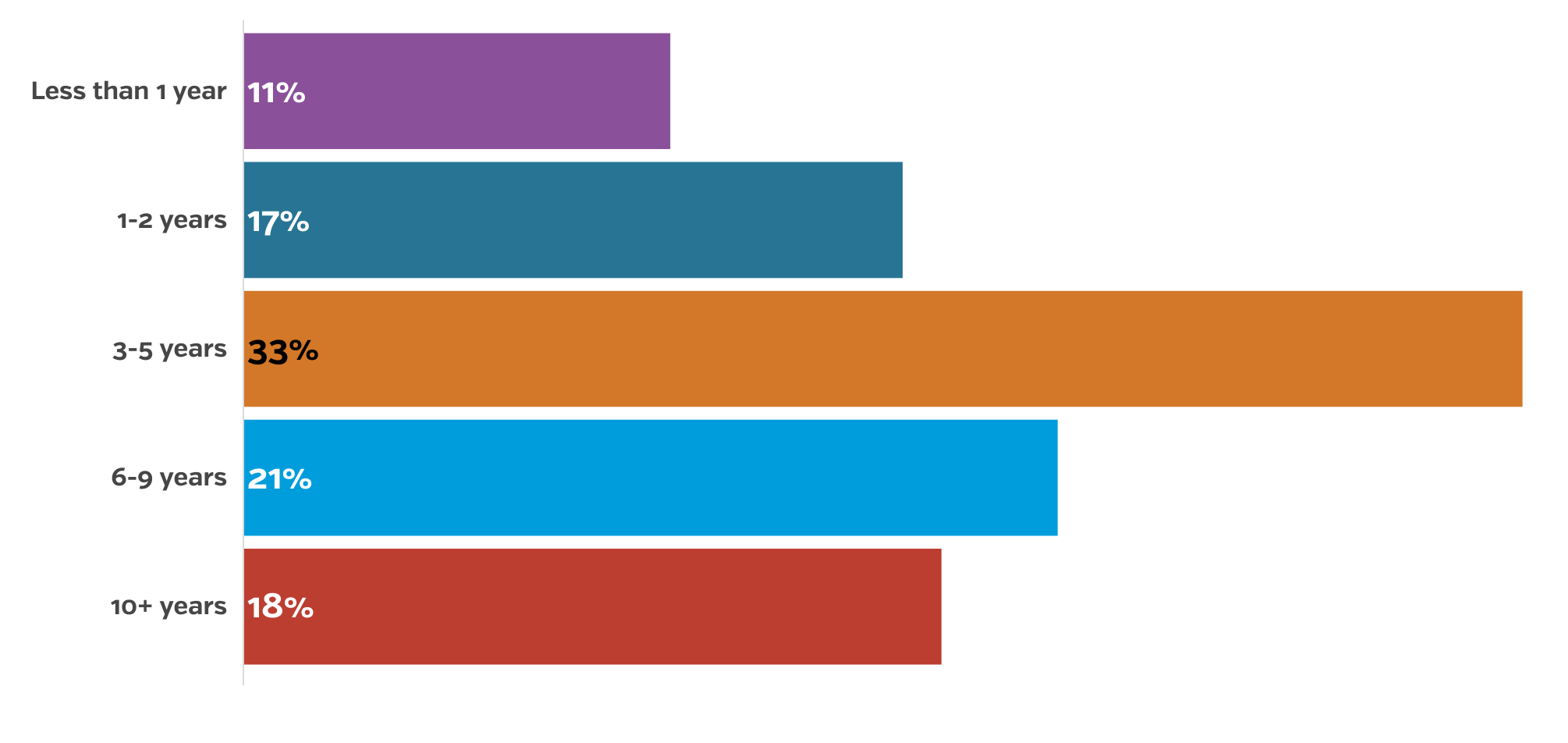
11% – Less than 1 year
17% – 1-2 years
33% – 3-5 years
21% – 6-9 years
18% – 10+ years
22% of those respondents noted that malware was the cause. 51% stated that their websites were down for 8-24 hours after the attack.
The leading form of attack currently, malware is any type of malicious software that allows unauthorized users access to sensitive and secure data and systems. Because malware attacks are useful for gaining access to secure networks and systems, it follows that attackers are leveraging other methods of exploiting the increased number of employees working remotely. These attacks include phishing attacks and efforts towards credential theft by way of social engineering efforts, with the intent of compromising login data and user access. These attacks are becoming increasingly prevalent because they are even more effective when targeted against personal devices and unsecured networks in use in remote work arrangements. Once accessed in the field, inconsistent security and compromised user accounts can allow malicious actors to shut down or compromise key systems, forcing the organization to go as far as shutting down their online assets such as websites and eCommerce platforms for as long as an entire day.
The tendency to target individuals over systems in the modern economy is rapidly changing the dialogue relative to how cybersecurity policies of small businesses are evolving. In fact, while a few high-profile software flaws have been the focus of cybersecurity experts throughout the start of 2022, overall more cyberattacks in the last few years have involved human error and manipulating user behaviors than the exploitation of software flaws. This is the primary reason why when cybersecurity specialists are included in conversations about how to best mitigate the impact of cybersecurity attacks, especially malware and personnel-focused attacks, employee training and education are often cited as the most effective methods that can be adopted by a business.
Most Common Cyberattacks Pre-COVID

12% – Credential theft/social engineering
20% – Phishing (Ex: Fraudulent email to gather sensitive data)
12% – Compromised/stolen devices
22% – Malware (Malicious software)
15% – Ransomware (Malicious software that blocks your company from accessing your systems)
14% – Insider attacks (Caused by malicious employees)
6% – Other
Hours of Website Being Down

31% – Less than 8 hours
51% – 8 hours to 24 hours
19% – 24+ hours
“While the finding that 1 in 3 businesses (operating for 3-5 years) have found themselves, victims of a cybersecurity attack, is a frightening one, it’s not, in fact, surprising.
For those organizations operating in start-up mode and reacting to the challenges associated with establishing and building their operations, brand and market, protecting their digital assets may not be top of the list of priorities. Leaders focused on growing a business are time-poor and, in many cases, simply don’t know what they don’t know.
This leaves many vulnerable, especially if everyday checks or security protocols are missed or forgotten. However, given the prospect of 8-24hrs of potential downtime following an attack, it can also prove hugely costly. At a time when you’re still trying to establish and grow brand loyalty, that’s reputational damage businesses can ill-afford.
Removing the burden of remembering those small yet vital steps to protect your business is crucial, and leaders can achieve this with technology. From leveraging mobile-first learning to ensure all staff is trained on recognizing malware or effective password hygiene to digitalizing essential security checks: streamlining and simplifying cybersecurity is vital for those newer businesses to stay protected.”
—Nicky Chenery, General Manager, UKIMEA, SafetyCulture
In order to better understand the challenges security professionals were dealing with prior to the pandemic, we asked them what sort of attacks were most prevalent before the outbreak of COVID-19.
“Phishing used to be the chart-topper before the advancement of the pandemic in 2019, and it still is one of the most commonly used methods by cyberbullies to target the details of the individuals. In addition to this, other methods like ransomware, fileless attacks, malware, Man-in-the-Middle attacks, attacks by malicious apps, denial of service attacks, and zero-day exploits were also prominent. Phishing is one of the easiest methods to go for the details of the target of the cyberattackers because through this method, it is easy to trick the users into entering an unsafe place via a malicious link or an attachment, and hence the companies were more vulnerable to this attack back then.
In 2022, the number of phishing attacks will be overtaken by ransomware attacks. It is noticeable by counting the number of attacks the companies have had in late 2021 and early. The COVID-19 pandemic has provided an environment that enabled ransomware to thrive for a long time. Some variants have also developed double extortion attacks to inflict more damage to the users. In order to fight off attacks moving into 2022, you should get your workforce educated. The NCASM event held every year provides free guidance to small businesses all around the nation to prepare themselves to be prepared against cyberattacks. You should also create a cybersecurity plan and have insurance for your plan. The former helps you retrieve your lost information in the event of a cyberattack, whereas the latter reduces the cost spent on retrieving the information.”
—Steve Anderson, CEO, Junk-Yard-Near-Me
“Phishing around tourism, incidents, or special financing offers. Zero-day vulnerabilities were used to attack large corporations. The targets: cryptocurrency exchanges (cryptocurrencies value growth), financial companies, and companies for which information is a primary resource. Attacks on small companies were a means of cyber groups’ promotion. This stemmed from the fact that successful cyberattacks were extremely profitable. In 2022, with the shift to support remote work, companies’ security systems became more vulnerable. Because many organizations were unprepared for this shift, their security teams were not always able to support a Zero Trust ideology and Zero Trust Network Access. In some cases, this meant that employees have been forced to work with protected data on computers with protection systems that were less functional than their office-based devices. Malicious cyber groups have received tons of targets for attacks, and the likelihood of obtaining valuable information has increased significantly. In order to mitigate or prevent these attacks, employers are increasingly adopting cloud technologies, as these services often integrate security services as part of the package.
For example, cloud office applications include an email service that is integrated not only with antivirus but also SandBox and Threat Intelligence services. Utilizing such services will reduce the likelihood of attracting the attention of these malicious groups.”
—Aliaksandr Latushka, Information Security Group Leader, Vention
“Prior to COVID-19, there were three major avenues of attack used by malicious attackers: phishing attacks, malware attacks, and password attacks, all of which are designed to allow attackers to compromise user credentials and gain a foothold within the target’s networks. These are the most common types of attacks as they can be executed on many people at a single time, allowing the attacker to have a bigger impact and achieve their targets very easily. With the pandemic, people’s reliance on the internet has grown tremendously. Attacks like phishing, credential thefts, ransomware attacks, etc. have grown in the area of education and research, healthcare, and ISP/MSP sectors. This is because people across industries such as healthcare and education increased their online activities in remote settings due to growing Covid-19 infection and lockdowns, respectively. These areas became easy targets, but employers can protect against attacks by keeping software updated, educating employees, using cloud storage in order to better secure data, and securing cybersecurity insurance.”
—Chun-Kai Wang, CEO, Kooapps (Developer of Snake.IO)
28% of small businesses have faced a cybersecurity attack since the pandemic started. 31% of respondents have also been in business for 3-5 years
The trend in attacks primarily targeted at small businesses in operation for three to five years prior to the outbreak of COVID-19 has continued throughout the pandemic and recovery period of 2022, largely due to many small businesses maintaining remote and hybrid work arrangements as standard operating practices. Notably, attacks have also increased against organizations in business for one to two years, as malicious actors are becoming increasingly aggressive and opportunistic with the increasing success they’ve had in gaining access to valuable data.
Years in Business
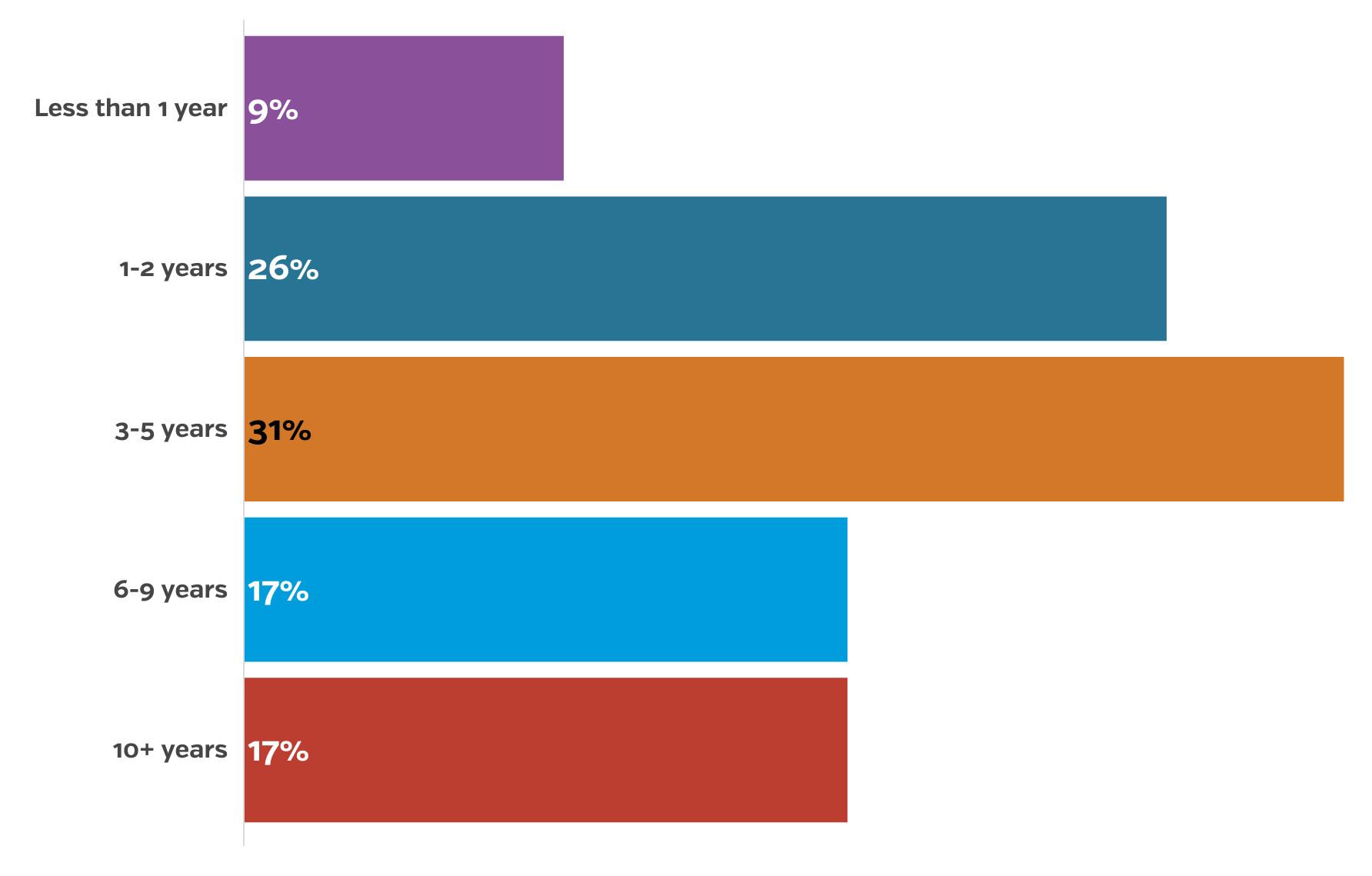
9% – Less than 1 year
26% – 1-2 years
31% – 3-5 years
17% – 6-9 years
17% – 10+ years
19% of those respondents said that ransomware was the cause of the attack and 48% noted that their websites were also down for 8-24 hours
While malware and social engineering attacks have been consistently leveraged, the COVID-19 pandemic has led to a concerning rise in ransomware attacks. The leading type of attack in 2022, ransomware attacks use other methods to gain a foothold within an organization’s networks and then are designed to lock out access to key data and systems unless the target agrees to pay a ransom to the attacker, often in the form of digital currency so as to obfuscate the intended recipients of payment. Malicious attackers have been inconsistent in keeping to the terms of these attacks, and have been known to either still delete the data or move on to sell the stolen data, making it very difficult for victims to fend off or respond to such attacks. Data backups combined with a comprehensive disaster recovery policy will help mitigate or minimize the damage done by a successful ransomware attack, but it’s rare that small businesses can rebound financially or operationally from the fallout from such attacks.
Most Common Cyberattacks in 2022
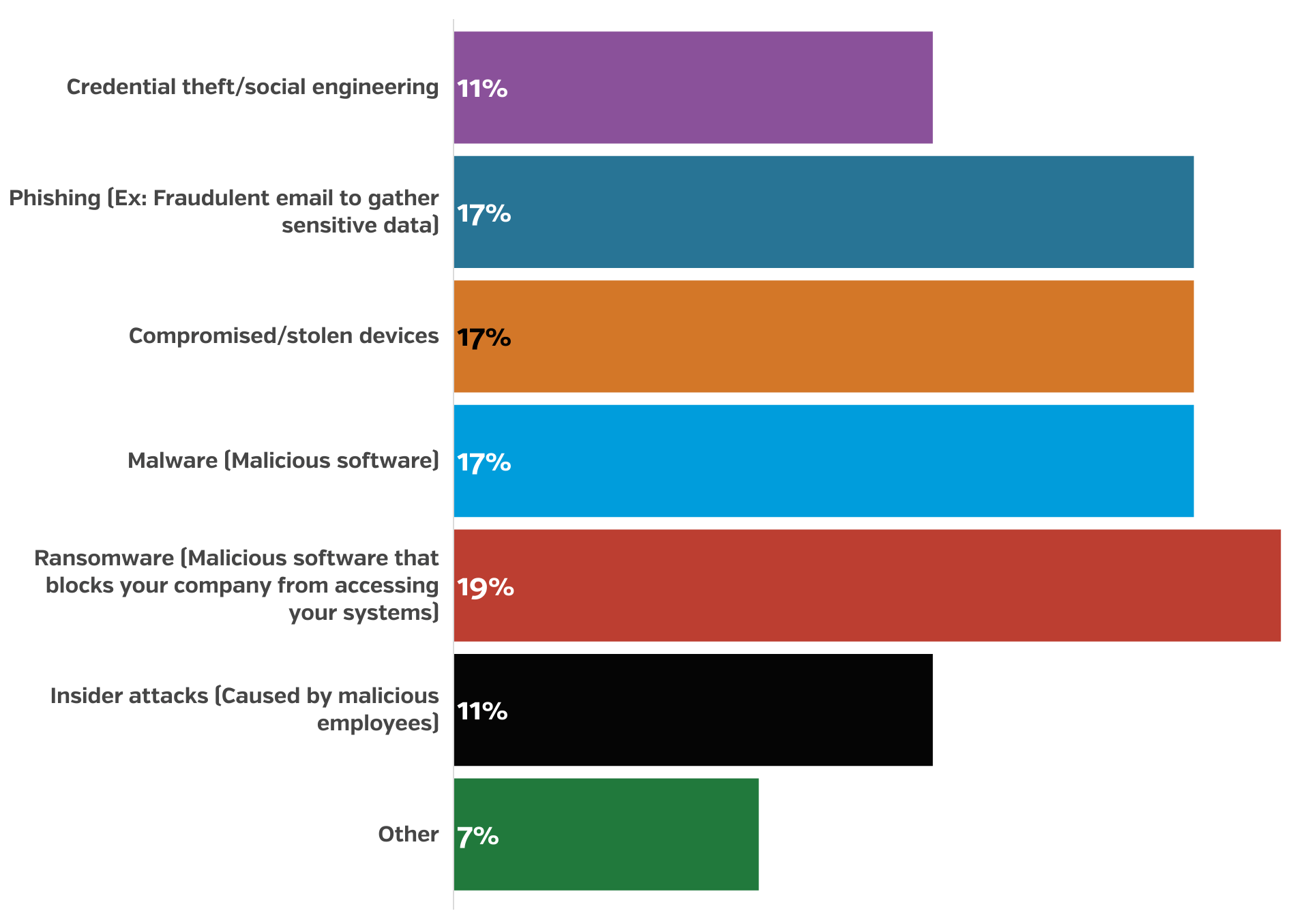
11% – Credential theft/social engineering
17% – Phishing (Ex: Fraudulent email to gather sensitive data)
17% – Compromised/stolen devices
17% – Malware (Malicious software)
19% – Ransomware (Malicious software that blocks your company from accessing your systems)
11% – Insider attacks (Caused by malicious employees)
7% – Other
Hours of Website Being Down

30% – Less than 8 hours
48% – 8 hours to 24 hours
22% – 24+ hours
“I am actually very surprised these numbers are not higher. As an IT company that is tailored to SMBs, we notice a majority of small business owners neglect their IT security. With companies implementing a more remote workforce approach after COVID, their infrastructure has become more vulnerable than ever. I would highly recommend SMBs to pay closer attention to this detail as it can truly damage their business.”
—Richard Guidry, President, Precise Business Solutions
We reached out to security professionals in the field to ask them to weigh in with their insight on how to prevent the types of attacks businesses are seeing increasingly in the wake of the pandemic and the adoption of remote work arrangements across industries.
“As a cybersecurity expert at vpnAlert, I believe that preparedness for cybersecurity begins with a thorough understanding of the internal and external vulnerabilities that can affect any business, how hackers gain access, including their various methods and motivations, and how to identify points of weakness. Learn about the various types of cyber fraud schemes and prevalent threats, including phishing and spoofing scams, social engineering, malware, system hacking, and pharming. Additionally, do not forget to update your antivirus software and other security applications on a regular basis. Updating your software will assist you in defending against the latest threats and securing your infrastructure. Additionally, educate your employees about the warning signs of a takeover, safe practices, and how to respond in the event of a suspected takeover. Assure that they use complex, one-of-a-kind passwords and maintain a clean desk environment free of personal and confidential information.”
—Bram Jansen, Chief Editor, vpnAlert
As we mentioned above, 2022 has been rife with the discovery of extremely wide-ranging software flaws that malicious actors have tirelessly exploited across the impacted software platforms. A number of professionals in the field gave insight on how to mitigate the impact of these flaws.
“Exploiting a network vulnerability when it is new and recently announced—before a patch is available and/or applied—is referred to as a Zero-day Exploit. Zero-day attackers take advantage of a newly discovered vulnerability within a small window of opportunity when no solutions or preventative measures are available. As a result, combating zero-day threats necessitates continuous monitoring, proactive detection, and flexible threat management techniques.”
—Matt Weidle, Business Development Manager, Buyer’s Guide
One of our professionals in the field perfectly summarized the challenges security professionals are facing in the post-COVID workplace.
“Before COVID-19, it was easier to develop cybersecurity policies, which is why cybercriminals before COVIC-19 had to be more clever. They had to set up a bot farm, spend long hours on breaking a website’s security, and other slower methods to infiltrate a network. However, COVID-19 forced many businesses to move to the digital sphere which meant that the digitization process was rushed, resulting in weaker security for sites, passwords, and accounts.
Many employees were initially inexperienced at using the Internet for work purposes and were unaware of the dangers, making it easy for malicious actors to send a virus via email. In 2022, cybercriminals still have an easier task, but more and more employers are allowing workers to set up home offices. With remote work part of many employers’ agendas for more than a year now, employees are becoming increasingly aware of threats and getting better at protecting their accounts and devices. The best advice for people looking for defense against cybercriminals is that you trust your IT specialist! They know how your company operates in the digital arena and, if they are good at their jobs, they will know how to educate you as to where potential threats may lurk.”
—Milo Miszewski, Founder & CEO, mDevelopers
Cybersecurity is an ever-evolving landscape, requiring cybersecurity professionals to understand and protect against a constant barrage of threat actors looking to manipulate and exploit attack vectors across increasingly complex and vulnerable attack surfaces. Prior to the pandemic, attacks were often complex and diverse as threat actors worked to circumvent the in-depth network security measures put into place by cybersecurity teams. With the quarantines and shutdowns pushing the adoption of remote work arrangements, cyberattackers have been able to focus their efforts more around social engineering and malware, with the intent of then launching ransomware attacks, attacks that have been both costly and increasingly destructive. This trend has led to the adoption of more advanced disaster recovery plans and prevention measures to minimize the impact of attacks.
Cybersecurity Threat Preparation and Prevention Measures
43% of small businesses feel confident that they’re financially prepared for a cybersecurity attack in 2022
The cost of attacks can vary greatly depending on the goals of the attack, so the respondents to our survey tell an interesting story of how ready they feel to recover from a cyberattack. While less than half of small businesses who responded to our survey feel financially prepared to recover from a cyberattack is an indicator of just how damaging these attacks have become, it only tells half the story. In fact, with cybercrime costing United States businesses more than $6.9 billion in 2021, the fiscal impact of cyberattacks becomes more clear when we look at the remaining 57% of respondents who either feel they need to improve their financial readiness to recover from an attack or they are completely unprepared to recover.

43% – My business is well-prepared financially to recover from a cyberattack
42% – Somewhat, but there’s room for improvement
15% – My business isn’t financially prepared to recover from a cyberattack currently
47% of businesses have also prepared by purchasing cyber liability insurance
Some of the bravado of the 43% of respondents who feel capable of recovering from a cyberattack can largely be attributed to the growing reliance upon cyber liability insurance that is designed to minimize the costs to businesses that fall victim to an attack. These plans are designed to help protect the customers of businesses by helping cover the costs for customer notification and providing services in the wake of a data breach to help protect consumer safety such as credit monitoring and repair. Insurance can also cover legal fees associated with an attack such as forensic analysis and representation as well as cover any fines that might be levied. Cyber liability insurance is also designed to help cover the loss in revenue, equipment replacement, and other costs associated with recovering from business disruption that can result from an attack.
This type of insurance has become crucial protection for small businesses and even enterprise operations, as the rising number of successful attacks on businesses with robust cybersecurity protocols in place proves that even the best-protected businesses aren’t safe from malicious actors intent on infiltrating targeted systems. It has also allowed businesses to regain their footing financially and still act in the best interests of impacted customers whose data is compromised in attacks, which can be an extremely expensive undertaking depending on the cause and scope of the breach.

47% – My business has purchased cyber liability insurance
36% – My business currently doesn’t own cyber liability insurance
17% – Unsure
When we asked our community of experts and owners how they felt about the insurance, many pointed to a number of recent ransomware events as proof of how crucial cyber liability insurance is becoming for small businesses across all industries. Many have come to realize that not even the smallest of operations are safe from attack, and cyber liability insurance is all that stands between recovery and closure in the aftermath of an attack. The plans can be tricky to set up properly, so our community members wanted to make certain readers understand some of the finer points around the insurance coverage around cybersecurity.
“An important reminder of the need for cyber liability insurance for your organization in light of the recent worldwide cyber-attack by WannaCry ransomware, which affected thousands of computers in over 100 countries. Today’s businesses rely heavily on technology and data. It’s impossible to predict the next digital threat since the digital world is always evolving. External dangers and internal flaws are both constant threats and if your network or data is hacked, your firm might be shut down. Cyber Insurance can secure your company and provide peace of mind.
Unfortunate events might result in grave repercussions. Remediation costs and company disruptions may rapidly increase after a data breach. In the meanwhile, consumers may sue industry authorities. A hacker may attack your computer system or website, halting your operation. Your company’s reputation may be harmed in any of these instances. The need for cyber liability insurance for your organization has never been greater. Call us to discuss your choices for cyber liability insurance.”
—Adam Crossling, Marketing Manager, zenzero
“While I believe cyber-liability insurance has become an integral part of any cyber-risk mitigation strategy, cyber-liability offerings are still relatively new, and as a result, many parties seeking coverage are unaware of the numerous critical factors to consider when selecting a policy. Complete any insurance application meticulously and as accurately as possible; providing inaccurate or false information on a cyber-liability insurance application can jeopardize your coverage severely. Even if a policy is issued, if you provide false information on the application, the policy can often be canceled retroactively after a claim is made, resulting in your claims being rejected and remaining unpaid.”
—Joe Manna, Content Manager, Alyce
“I think businesses should consider how cyber liability insurance can help them protect their digital assets as more businesses use customers’ online data. Operating a business, regardless of its size or industry, requires a significant amount of effort and discipline. And ensuring that your daily operations run smoothly requires you to invest the appropriate amount of time and resources. It is critical to safeguard those investments, which is why businesses carry insurance to cover a variety of business assets.
Cyber liability insurance protects your digital assets, ensuring that you do not lose significant amounts of money or are forced to shut down your business entirely as a result of the breach. By purchasing this policy, you are transferring some of the risks associated with a cyberattack to someone else rather than taking them on yourself. Additionally, having Cyber Liability insurance protects you from the financial consequences of a business interruption caused by a cyberattack. Additional layers of protection should be implemented by businesses. To keep hackers at bay, it is critical to adhere to industry standards for data security and to ensure that your employees follow company security protocols.”
—Daniel Hedegaard, Head of Press, CoolParcel
45% of businesses operating partially or fully remote are currently taking extra security precautions. 14% of respondents are investing more heavily in firewalls and antivirus software
If a company wants to ensure that its assets and data remain secure while much of the workforce is working remotely, they must implement additional steps and precautions for their employees to access company assets through the Internet that users don’t necessarily utilize in their daily lives. Because workers are remote and working beyond the confines of secured networks, small businesses are leaning more heavily on firewalls and antivirus software. Firewalls are configurable security tools that help to manage and block unauthorized web traffic but permit outgoing communications from sources with proper authorization.
Antivirus software scans for and isolates malicious software, keeping it from infecting other systems on the network or gaining access to company assets. However, the leading tools being used by small businesses to secure systems relative to the known cybersecurity threats facing remote workers have been web vulnerability scanning tools. These tools scan digital assets and software platforms for known vulnerabilities tracked by organizations such as MITRE or NIST, allowing your cybersecurity team to identify and take actions to address those vulnerabilities as patches and workarounds become available. Overall, this helps to mitigate many of the risks posed by a remote workforce.
Remote Business Precautions

45% – My business is partially/fully remote and we are taking extra security precautions as a result
33% – My business is partially/fully remote and we aren’t concerned about additional risk(s)
22% – My business is fully in-person, remote cybersecurity risks aren’t a concern at this time
Aside from vulnerability scanning tools, firewalls, and antivirus, cybersecurity professionals supporting remote workforces have leaned on a number of other methods for securing company data. Some highlights revealed by our survey include the use of encryption tools, which converts and encodes data before transmitting it across the Internet and allows receiving systems to decrypt and read the data. Managed detection services also made an appearance in the tools being leveraged, which are outsourced services that search for threats and vulnerabilities in your systems and help your team address those vulnerabilities. Similarly, penetration testing services can be hired to simulate a threat actor breaching your systems in order to identify gaps or holes; pen testers then present their findings to your team to provide the necessary information on how systems can be better secured moving forward. The chart below shows the other types of precautions respondents have claimed to have put into play in order to support their remote workforces.
Precaution Types

“As companies and organizations have moved increasingly from headquarters and branch offices to a remote home office environment, this new work model has exposed serious weaknesses in cyber security protection. Traditionally, organizations’ digital assets were behind robust, industrial-strength firewalls that protected both headquarters and branch offices. This new remote work model demands much stronger protection of data in-home office computers. Over the next several years, more robust home office firewalls and strong EDR products will be delivered to better protect the remote worker.”
—Don Wisdom, President, Datalink Networks
“In a remote-first world, small businesses need to think about security awareness for their users as they are no longer on-site to ask questions or mention that something seems suspicious. Small businesses’ focus should first be on raising the employee’s security awareness, during which time you are showing employees how to protect themselves and their families with their data and their personal information; it will then carry over to their professional environment. For example, by providing your stakeholders with a password manager with multifactor authentication capabilities, you can get them comfortable using that layer of protection for their accounts and then implement that in the business for business accounts.
Another example of helping employees with security awareness can be to make them aware of phishing and other social engineering attacks which could affect them personally, as this will also make them aware of them in the business environment. As leaders in the background, you also set the organization’s tone, so if you demonstrate a safety-first approach to security and operations, your employees will model that. Other layers of protection could include backup capabilities, endpoint security capabilities, and validation processes for important company transactions.”
—Christophe Foulon, Cybersecurity Speaker, CPF Coaching
We wanted to give more of our community of experts a chance to provide their guidance and insight, so we asked them what precautions they felt small business cybersecurity teams should be taking in 2022 to prevent or at least decrease the chances of cyberattacks.
“Home networks are often less secure than office networks, so make sure your employees have the appropriate solutions in place, such as a VPN that can protect IP addresses, encrypt data, and conceal your employees’ location. This provides an additional layer of security for your workers, allowing you to keep fraudsters at bay while also securing home networks. Regardless of where your employees might be working, you should make it a policy to not send sensitive information by email or text. Emails, team chat, and text messages are all ways of communication that are simple for your team to use; yet, they can be intercepted by malicious actors. An encrypted file sharing solution, which can be integrated into your company’s technology stack, is a good choice for sharing sensitive data.”
—Tim Parker, Director of Marketing, Syntax Integration
“Remote workers are back to a break-neck work pace, most use multiple devices and they face upwards to 1,000 electronic messages a day. They’re highly susceptible to doing the wrong thing – by accident. As a precaution, businesses should deploy an automated, measurable, and meaningful way to sharpen their employee’s cyber threat skills. Not all security awareness training methods are created equal. It is a necessary evil and insurance brokers and government regulations now require it. But if you’re approaching it to ‘check the box,’ you’re missing out on closing the largest security gap you have: your people. Create a human firewall by making security training a priority, make it simple and fun, and you’ll be surprised how much lower your risk measurably reduces—as well as your insurance premiums.”
—Ray Steen, Chief Strategy Officer, MainSpring, Inc.
“Before developing a long-term remote work strategy, small businesses should create comprehensive remote work policies. There should be no ambiguity regarding what employees are expected to do while working remotely. Furthermore, this document should explain how remote work privileges are governed by cybersecurity. That means describing who can access what systems and data remotely. Additionally, it should provide for auditing employee-owned devices and set minimum standards for those devices. Work from home offers tremendous flexibility, so many people choose it.
For a change of scenery, employees can go to their local cafe to work or get their work done at home. However, employees must be careful when connecting to a public Wi-Fi network. A virtual private network (VPN)—a service that allows users to create a secure, encrypted tunnel between their devices and the internet—is one way to solve this problem. There is no doubt that remote work will play a significant role in the future of business. Data security is a major bottom-line threat for companies that ignore it from day one. It is vital for small businesses. But by reconsidering their remote work procedure, small businesses can handle that danger and move onwards with conviction.”
—Tristan Harris, Demand Generation Senior Marketing Manager, Thrive Agency
34% of small businesses aren’t specifically concerned about Russian cyberattacks. However, of the respondents that are concerned, 24% stated that they’re further educating themselves and their employees on cybersecurity threats and prevention measures.
International conflicts can cause significant spikes in cyberattacks across multiple industries, especially for organizations either operating internationally or known to be integral to infrastructure and vital services. In addressing cybersecurity readiness, we would be remiss if we didn’t address how professional organizations were responding to and protecting themselves against the increased cyber activity against United States businesses in response to sanctions against Russia. Of the 64% of respondents who have at least a moderate concern regarding Russian cyberattacks, just under a quarter of them are taking measures to insulate themselves.
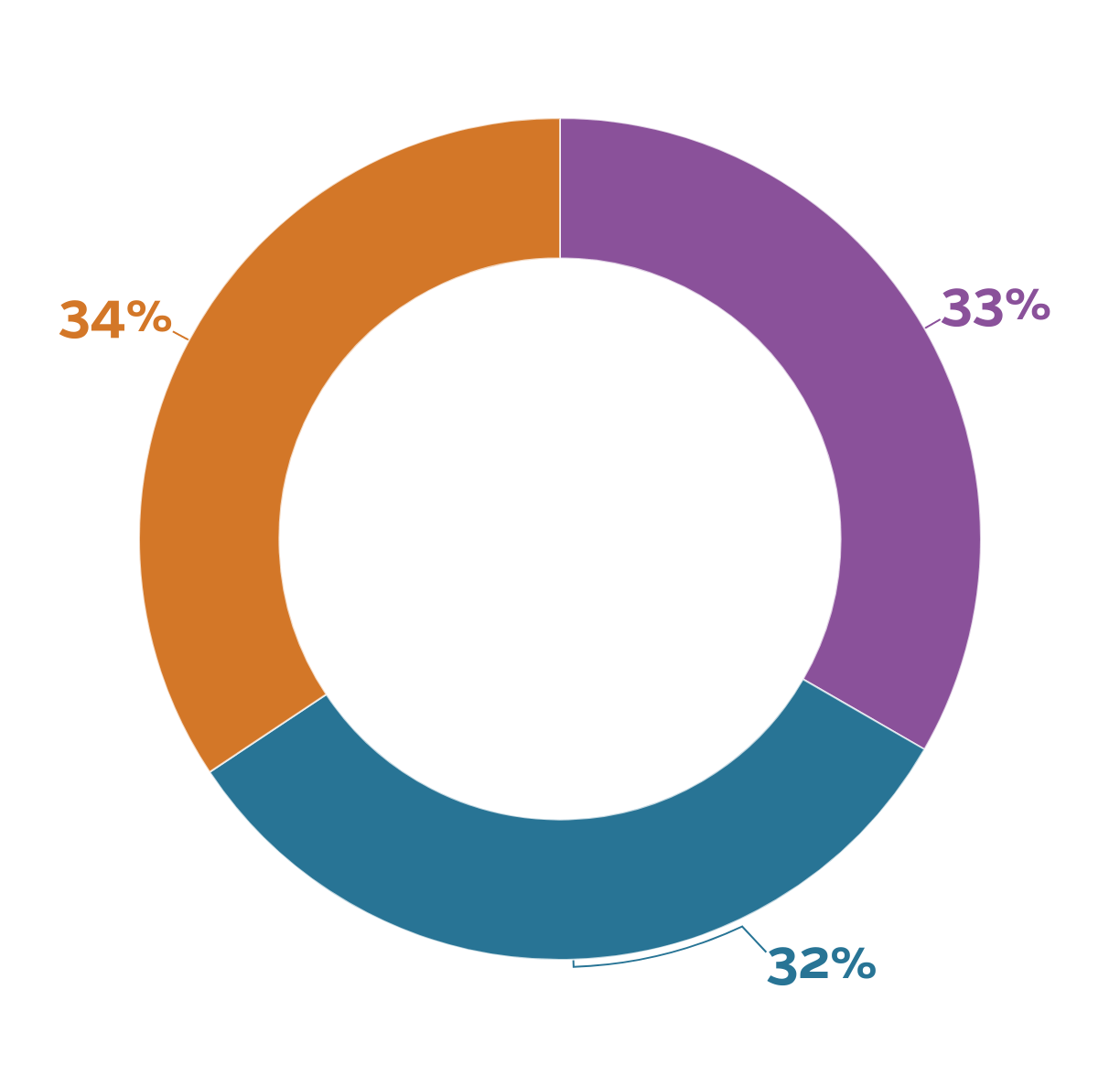
33% – Russian cyberattacks are a large concern for my business
32% – Russian cyberattacks are a moderate or minor concern for my business
34% – I’m not particularly concerned about Russian cyberattacks
The small business teams that are adding layers to their cybersecurity protocols in response to the Russian-Ukraine conflict are bringing in additional talent and expanding cybersecurity responsiveness through the use of third-party service providers. Others are shoring up their fiscal preparedness through expanded cyber liability insurance policies. A majority of our respondents in this case, however, are splitting their efforts between bolstering their tech stacks with new tools and software and improving the skills and awareness of staff through education and training. This is indicative of the two schools of thought prevailing in cybersecurity, necessitating small businesses to find a balance between giving their cybersecurity professionals the necessary tools to do the work against the need to educate and inform workers of best practices.
Extra Precautions

15% – Hire more in-house IT experts
15% – Expand my work with a third-party provider
17% – Purchase new insurance or increase my cyber liability insurance policy
23% – Upgrade my cybersecurity tools/software
24% – Further educate myself and/or my employees on cybersecurity threats and prevention measures
6% – Other
Any international conflict that could escalate into a global crisis is apt to cause concern across multiple industries, especially when a major international power ramps up its malicious cyber activity against the countries imposing sanctions against it. We wanted to explore more in-depth how small business owners and security experts feel about the increased frequency of attacks and how best to protect themselves.
“The Shields Up advance notice is directed toward the U.S. private sector, and the organization is partly founded on Russia’s denial of service attack on Ukraine by its military. There is no denying the cyber threat is genuine. Small businesses should take cyberattacks seriously. They should invest in cybersecurity and hire a cybersecurity expert to make their business network penetration free. They should also focus on data security and should do security checks regularly. Even though your independent company may not be compromised directly, public and private sectors depend on it to remain functional. Also, this is where the term collateral danger comes into play. Assuming these associations are gone after or get attacked, your small business will suffer. Apart from Russia, cybercriminal associations have expressed their full help to the Russian government. These cybercriminals are in part liable for significant hacks and ransomware assaults occurring all over the planet. This is why small businesses should stay cautious.”
—Lyle Florez, Founder, EasyPeopleSearch
“Cyberwarfare these days is frequently connected with apocalyptic visions of burned-out infrastructures and week-long outages. These dangers are real, but they are luckily rare. Long-term low-level interruptions to essential infrastructure, as well as a generally damaged cyberspace and tech environment, might be a much more feasible scenario for a larger political cyberwar. As leaders, we must embrace cyber resilience strategies and business continuity measures to prepare for such interruptions. In pursuit of that effort, it’s important that we integrate cybersecurity knowledge into the board of directors. At the board level or equivalent, all businesses should have established a corporate resilience manager. This individual will need to look at the situation from a broad viewpoint, taking into account additional dangers such as pandemic-related situations. Consider having the Chief Information Security Officer (CISO) personally present, or at the very least arrange frequent briefings for the full board, to ensure cyber is appropriately represented. Overall, the resilience management and CISO should consider involving the board of directors in tabletop exercises to simulate digital disruption and the decisions that it may necessitate. The World Economic Forum contributed to the development of the Principles for Board Governance of Cyber Risk in order to assist firms in becoming more robust to cyberattacks.”
—Michael Hess, eCommerce Strategy Lead, Code Signing Store
“Small businesses worried about cybersecurity should focus on the basics. Amongst those practices should be zero trust and defense in depth. This means that your organization should assume a breach and verify it explicitly, and erect multiple forms of defense. Not the same type of defense multiple times, but rather different forms of defense specifically to address a threat type. A good analogy to this is to think of the castle, with a moat—each is there to defend against a specific intrusion type. In the Russian/Ukraine crisis, while State and critical infrastructure may be active targets of cyber warfare, small businesses aren’t targets. They’re simply collateral damage. Cybercriminals are leveraging the fear around war and cybersecurity to create chaos and gain an easy profit. This means cybercriminals are relying on the path-of-least resistance when it comes to small businesses. This is why I suggest to my Small to Medium Businesses (SMB) clients that they should continue to focus on cybersecurity basics and apply the security in depth principle.”
—Sijia Wang, Managing Partner, SiFr Consulting
The rapidly evolving capabilities of threat actors, both domestic and international, make damaging data breaches and crippling cyberattacks a matter of when, not if, for many organizations. Even the most prepared cybersecurity teams could fall prey to sophisticated attacks when carried out by attackers intent on doing damage to targeted networks.
As we discussed earlier, however, the rising prevalence and reliance on cyber liability insurance policies mean that businesses must do all they can to show that they are aligned with the most effective mitigation strategies possible in order to secure coverage. This has become increasingly difficult for organizations as remote work arrangements have become the standard across a number of industries. As many of the experts’ responses suggest, it’s crucial to start with the basics and focus on educating employees so that they become advocates for cybersecurity and less of a liability.
Cybersecurity Must Be An Integral Part of Your Risk Mitigation Strategy in 2022
In the past, it was common practice for IT teams to treat cyberattacks as a shortcoming or fault in technology systems or poorly configured networks. Organizationally, leadership would then secure the latest and best technology to deploy in hopes that it would protect internal systems. Today, an increasingly distributed workforce working remotely in the field across unsecured devices and connections means that cybersecurity teams must convince leadership to take a different approach to mitigate the impact of inevitably successful attacks.
Small business cybersecurity professionals have widely taken the stance that the field has become largely about risk mitigation and reducing risk across multiple channels. This requires not only the adoption of cutting-edge technologies and software platforms but also ensuring employees are well educated on the role they play in keeping their organization’s digital assets secure.
If your team is looking to expand your cyber capabilities through a third-party managed services provider, you can find the resources you need at UpCity’s marketplace of cybersecurity companies. It’s crucial that you take the steps necessary in 2022 to shore up your digital barriers and do all that you can to protect your brand’s assets.
UpCity’s Survey Method
UpCity used Pollfish to survey 600 business owners and IT professionals across the United States on their 2022 cybersecurity plans, priorities, and budgets.
Twenty-three percent of respondents have 101-250 employees, followed by 50-100 (21%), 2-5 (15%), 26-50 (15%), 6-10 (13%), and 11-25 (13%).
Fifty-four percent of respondents are male and forty-six percent are female.

